What is Ethical Hacking?
What is Ethical Hacking? | Ethical Hacking for Beginners | Edureka
This Edureka video on “What is Ethical Hacking” will give you an introduction to Ethical Hacking. This is a beginner’s tutorial covering all the fundamentals of Ethical Hacking.
Hacking is the process of finding vulnerabilities in a system and using these found vulnerabilities to gain unauthorized access into the system to perform malicious activities ranging from deleting system files to stealing sensitive information. Hacking is illegal and can lead to extreme consequences if you are caught in the act. People have been sentenced to years of imprisonment because of hacking.
Nonetheless, hacking can be legal if done with permission. Computer experts are often hired by companies to hack into their system to find vulnerabilities and weak endpoints so that they can be fixed. This is done as a precautionary measure against legitimate hackers who have malicious intent. Such people, who hack into a system with permission, without any malicious intent, are known as ethical hackers and the process is known as ethical hacking.
So now that we know what exactly ethical hacking is, and who ethical hackers are, let’s go over the different types of hackers.
What are the types of Hackers?
Hackers can be segregated according to their intent.
White Hat Hacker
 It is another name for an Ethical Hacker. They hack into a system with prior permission to find out vulnerabilities so that they can be fixed before a person with malicious intent finds them.
It is another name for an Ethical Hacker. They hack into a system with prior permission to find out vulnerabilities so that they can be fixed before a person with malicious intent finds them.
Black Hat Hacker
 They are also known as crackers, who hack in order to gain unauthorized access to a system & harm its operations or steal sensitive information. It’s always illegal because of its malicious intent which includes stealing corporate data, violating privacy, damaging the system etc.
They are also known as crackers, who hack in order to gain unauthorized access to a system & harm its operations or steal sensitive information. It’s always illegal because of its malicious intent which includes stealing corporate data, violating privacy, damaging the system etc.
Grey Hat Hacker
 They are a blend of both black hat and white hat hackers. They mostly hack for fun and exploit a security weakness in a computer system or network without the owner’s permission or knowledge. Their intent is to bring the weakness to the attention of the owners & earning some bug bounty.
They are a blend of both black hat and white hat hackers. They mostly hack for fun and exploit a security weakness in a computer system or network without the owner’s permission or knowledge. Their intent is to bring the weakness to the attention of the owners & earning some bug bounty.
Suicide Hacker
 A suicide hacker is a person who works with the intent to bring down major corporations and infrastructure. These kinds of hackers are not scared of the consequences of their actions as they mostly work with a vengeance in their mind. These people are also known as hacktivists.
A suicide hacker is a person who works with the intent to bring down major corporations and infrastructure. These kinds of hackers are not scared of the consequences of their actions as they mostly work with a vengeance in their mind. These people are also known as hacktivists.
What are the different types of hacking?
Now that we have discussed the various types of Hackers, let’s go over the different types of hacking. We can segregate hacking into different types depending on what the hacker is trying to achieve.
Website Hacking
 Hacking a website means taking unauthorized control over a web server and its associated software such as databases and other interfaces.
Hacking a website means taking unauthorized control over a web server and its associated software such as databases and other interfaces.
Network Hacking
Hacking a network means gathering information about a network by using tools like Telnet, NS lookup, Ping, Tracert, Netstat, etc. with the intent to harm the network system and hamper its operation.
Email Hacking
 This includes gaining unauthorized access to an Email account and using it without taking the consent of its owner for sending out spam links, third-party threats, and other such harmful activities.
This includes gaining unauthorized access to an Email account and using it without taking the consent of its owner for sending out spam links, third-party threats, and other such harmful activities.
Password Hacking
 This is the process of recovering secret passwords from data that has been stored in or transmitted by a computer system.
This is the process of recovering secret passwords from data that has been stored in or transmitted by a computer system.
Computer Hacking
 This is the process of stealing computer ID and password by applying hacking methods and getting unauthorized access to a computer system.
This is the process of stealing computer ID and password by applying hacking methods and getting unauthorized access to a computer system.
Phases of Ethical Hacking
Like every discipline out there in the world, ethical hacking is divided into distinct phases. Ethical hacking has 6 distinct phases. These phases are not strict rules, but more like a guideline to be followed.
Reconnaissance
Reconnaissance is the process of information gathering. In this phase, the hacker gathers relevant information regarding the target system. These include detecting services, operating systems, packet-hops to reach the system, IP configuration etc. Various tools like Nmap, Hping, Google Dorks etc are used for reconnaissance purposes
Scanning
In the scanning phase, the hacker begins to actively probe the target machine or network for vulnerabilities that can be exploited. Tools like Nessus, Nexpose, and NMAP are widely used by hackers in this process.
Gaining Access
In this phase, the vulnerability located during scanning is exploited using various methods and the hacker tries to enter the target system without raising any alarms. The primary tool that is used in this process is Metasploit.
Maintaining Access
This is one of the most integral phases. In this phase, the hacker installs various backdoors and payloads onto the target system. Just in case you don’t know, Payload is a term used for activities performed on a system after gaining unauthorized access. Backdoors help the hacker gaining quicker access onto the target system in the future.
Clearing Tracks
This process is an unethical activity. It has to do with the deletion of logs of all the activities that take place during the hacking process. Nonetheless, Ethical Hackers still have to perform this phase to demonstrate how a Black Hat Hacker would go about his activities.
Reporting
Reporting is the last step of finishing the ethical hacking process. Here the Ethical Hacker compiles a report with his findings and the job that was done such as the tools used, the success rate, vulnerabilities found, and the exploit processes.
Reconnaissance
Okay, so let’s talk a little bit more about Reconnaissance. I’ve already mentioned that it is the process of gathering information about the target system, but what kind of information are we trying to gather? Well, to list them out would be a task but they can be boiled down to the following
- Gather initial information
- Determine the network range
- Identify active machines
- Discover open ports and access points
- Fingerprint the operating system
- Uncover services on ports
- Map the network
Active Reconnaissance
Active Reconnaissance refers to the process when you, the hacker, directly interact with the computer system to gain information. This information can be relevant and accurate. But there is a risk of getting detected if you are planning active reconnaissance without permission. If you are detected, the system admin can take severe action against you and trail your subsequent activities.
Passive Reconnaissance
Passive Reconnaissance, on the other hand, doesn’t directly interact with the computer. This process is used to gather essential information without ever interacting with the target systems.
What is Footprinting?
Footprinting is basically the first step where hacker gathers as much information as possible to find ways to intrude into a target system or at least decide what type of attacks will be more suitable for the target.
Footprinting is a part of the reconnaissance process which is used for gathering possible information about a target computer system or network. Footprinting could be both passive and active. Reviewing a company’s website is an example of passive footprinting, whereas attempting to gain access to sensitive information through social engineering is an example of active information gathering.
During this phase, an ethical hacker can collect the following information
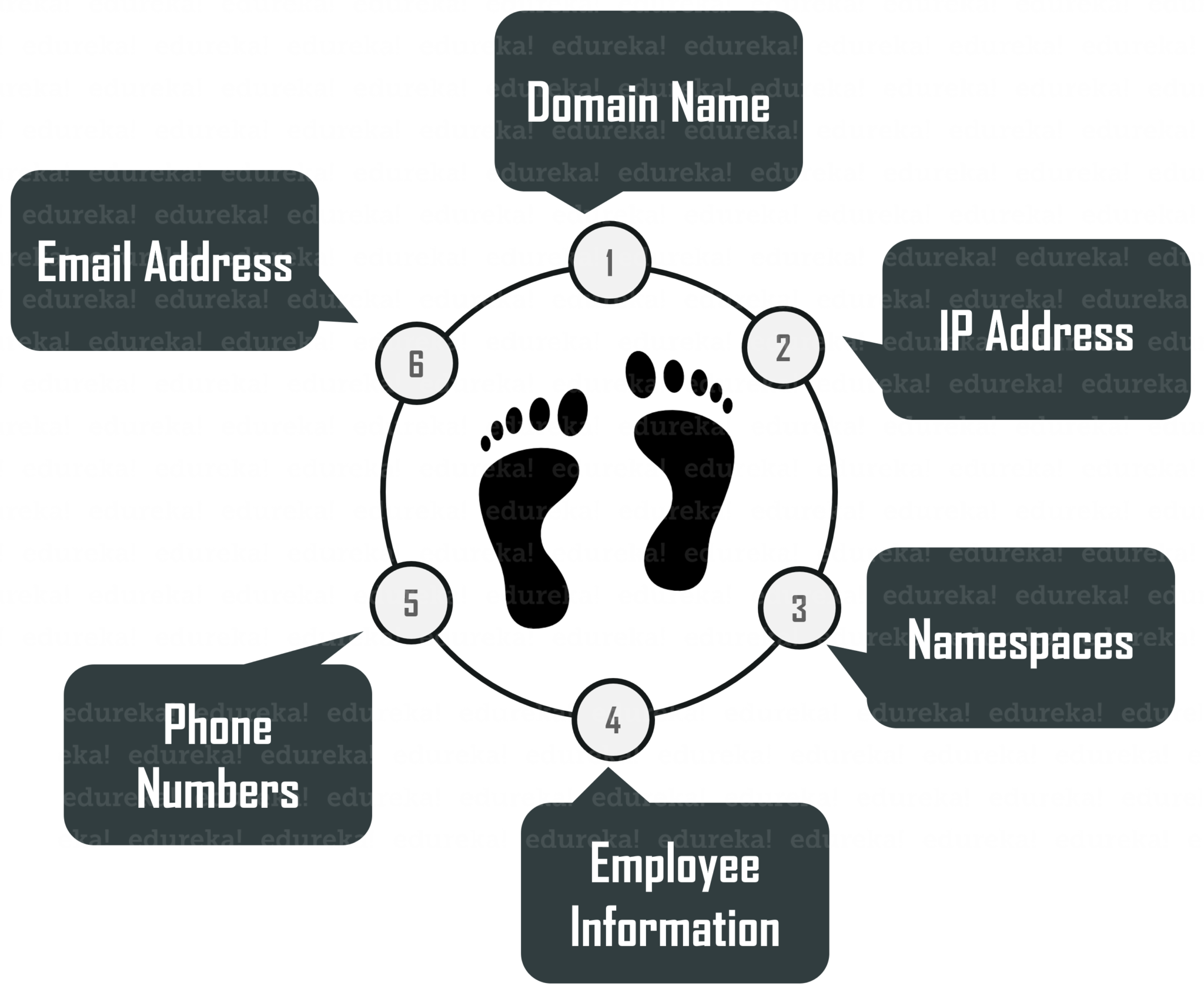
Foot printing – What is ethical hacking – Edureka
General foot printing is really simple and even an everyday user could do it using websites like whois.com, ip2location.com, archive.org etc
What is Fingerprinting?
Fingerprinting, in ethical hacking, refers to any method that is used to determine the operating system that is being run on the target computer. Fingerprinting, much like Foot printing is both active and passive
Active Fingerprinting
Active fingerprinting is accomplished by sending specially crafted packets to a target machine and then noting down its response and analyzing the gathered information to determine the target OS. In the following section, we have given an example to explain how you can use NMAP tool to detect the OS of a target domain.
Passive Fingerprinting
Passive fingerprinting is based on sniffer traces from the remote system. Based on the sniffer traces (such as Wireshark) of the packets, you can determine the operating system of the remote host. Before attacking a system, it is required that you know what operating system is hosting a website. Once a target OS is known, then it becomes easy to determine which vulnerabilities might be present to exploit the target system. Fingerprinting is done by analyzing various factors of a packet
- TTL − What the operating system sets the Time-To-Live on the outbound packet.
- Window Size − What the operating system sets the Window Size at.
- DF − Does the operating system set the Don’t Fragment bit.
- TOS − Does the operating system set the Type of Service, and if so, at what.
By analyzing these factors of a packet, you may be able to determine the remote operating system. This method is not 100% accurate and works better for some operating systems than others.
Okay, guys, this brings us to the end of this “What is Ethical Hacking?” blog. This is the first blog in a long list of ethical hacking blogs that I’m going to publish. For more information regarding cybersecurity, you could check out my other blogs. If you have any doubts or queries regarding this particular article, leave a comment in the comments section below!
If you wish to learn Cybersecurity and build a colorful career in cybersecurity, then check out our Cybersecurity Certification Training which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in-depth and help you achieve mastery over the subject.
You can also take a look at our newly launched course on CompTIA Security+ Certification



Comments
Post a Comment